DeFi protocol Arcadia Finance has experienced a significant attack resulting in the loss of hundreds of thousands of dollars.
The outlined exploit highlighted critical code vulnerabilities within the protocol, draining funds from both the Ethereum and Optimism chains.
Code Vulnerabilities and Exploitation
Arcadia Finance, a non-custodial leveraged farming protocol facilitating cross-margin accounts on-chain, fell victim to an attacker who exploited vulnerabilities within its code.
Blockchain intelligence firm PeckShield discovered that the lack of untrusted input validation and reentrancy protection allowed the hacker to access Arcadia Finance’s wallets and execute instant liquidations.
Untrusted input refers to data or information from user inputs, network communications, or external sources outside the application’s control. The purpose of untrusted input validation is to ensure the security and integrity of a system by checking and sanitizing the input before using it in any operations or processing.
Reentrancy protection is a security measure implemented o prevent unauthorized and potentially malicious reentrant calls. Reentrancy refers to the ability of a contract to call itself or call another contract within its execution flow.
In the context of smart contracts, reentrancy vulnerabilities occur when an external contract can make recursive calls into the vulnerable contract before the ongoing execution is completed.
A lack of untrusted input validation and reentrancy protection can lead to security breaches and exploitation of vulnerabilities. Attackers may manipulate the input data by injecting malicious code, random characters, or special sequences that could trick the application into executing unintended actions or accessing unauthorized resources.
Furthermore, reentrancy attacks often exploit race conditions where the state of a contract can be modified multiple times during a single execution. Attackers take advantage of this by calling back into the vulnerable contract at certain points in the execution flow, potentially causing unintended consequences or allowing unauthorized access to critical resources.
The Attack and Post-Exploit Actions
The hacker initiated the attack on both the Ethereum and Optimism chains, draining approximately $455,000 from Arcadia Finance. The stolen funds on the Optimism chain were washed through the Tornado cash protocol, while the funds on the Ethereum chain remained in the hacker’s wallet.
The root cause of the exploit was identified as a missing reentrancy check during the liquidation of a vault, which allowed the attacker to manipulate the assets and debt within the system. Contracts related to Arcadia liquidity pools have been paused, preventing further debt transactions, and the interest rate has been set to 0 to avoid interest accumulation.
Following the attack, Arcadia Finance’s total value locked (TVL) plummeted from just over $600,000 to less than $150,000.
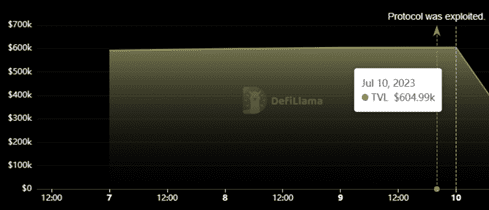
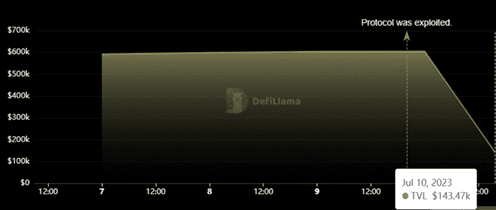
The priority for the Arcadia team is the recovery of the lost funds, and they are collaborating closely with law enforcement agencies and security experts to identify the hacker and retrieve the misappropriated funds.
Arcadia Finance has collaborated with several security teams, including BlockSec, Hexagate, PeckShield, and law enforcement agencies, to investigate both on-chain and off-chain data.
Conclusion
The attack on Arcadia Finance serves as a reminder of the risks associated with code vulnerabilities in decentralized finance protocols. The protocol’s prompt response, collaboration with security experts, and engagement with law enforcement agencies demonstrate their commitment to recovering the stolen funds. As the investigation progresses and security measures are strengthened, the DeFi community awaits further updates on resolving this incident.














