- Waltio received a ransom threat tied to leaked crypto tax user data
- Hackers are increasingly targeting personal crypto-related metadata
- Non-custodial platforms are now prime targets for extortion
Waltio, a well-known French crypto tax platform, is dealing with a problem far removed from spreadsheets and filing deadlines. The company has confirmed it received a ransom threat after a hacker group claimed to possess sensitive user data, including email addresses linked to crypto tax information. Even without custody of funds, the incident highlights how personal crypto-related data has quietly become a high-value asset for cybercriminals.
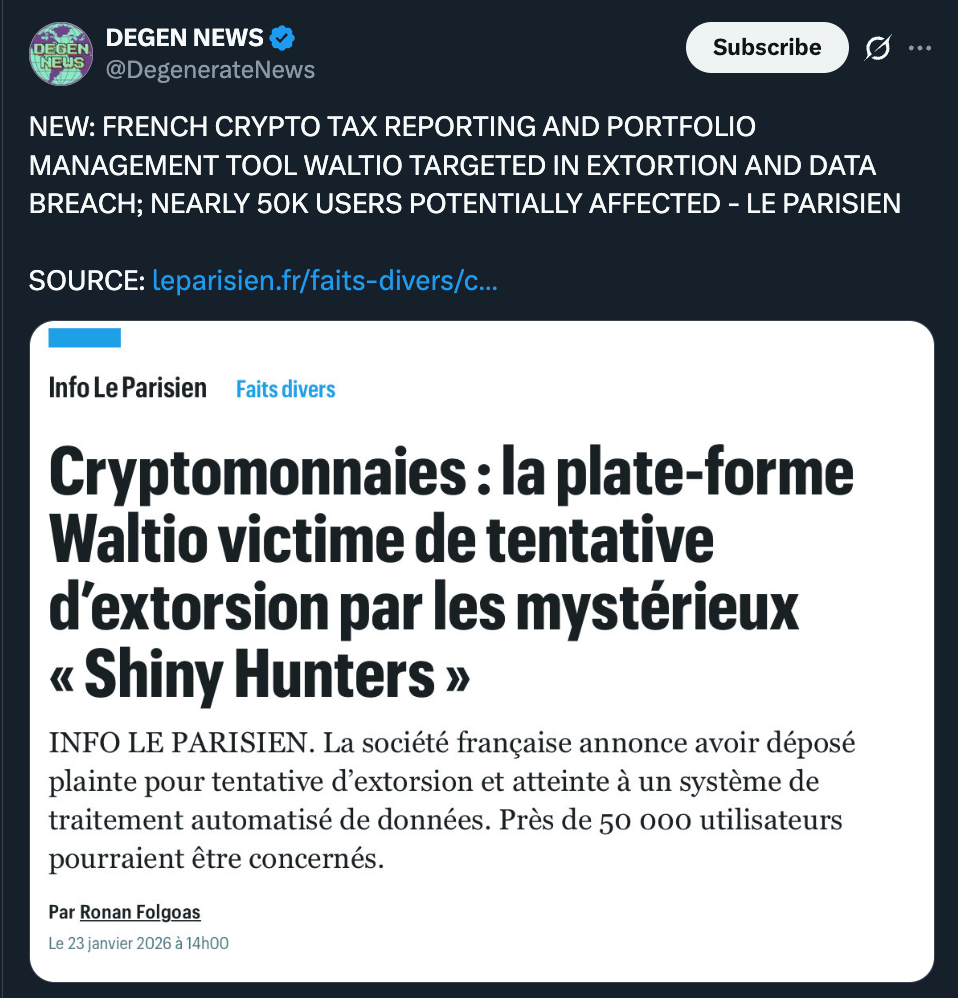
Why Waltio Was an Attractive Target
Waltio built its reputation by simplifying crypto tax reporting, aggregating portfolio data and calculating obligations automatically. That convenience comes with a tradeoff. Platforms like this sit on detailed financial metadata tied to real identities. According to the threat, the attacker group known as Shiny Hunters claims to have access to thousands of user records.
This isn’t a random operation. Shiny Hunters has been associated with major corporate breaches and extortion campaigns in recent years. Their playbook is familiar. Steal data, threaten disclosure, and apply pressure where it hurts most, reputational and personal exposure.
The Real Risk Isn’t Private Keys
Crypto security conversations usually revolve around wallets and private keys. That focus misses a growing vulnerability. Your identity, tax history, and wallet associations can be just as dangerous in the wrong hands. Even if a platform never touches your funds, the data it stores can be used to intimidate, profile, or coerce.

Waltio has stated there’s no evidence so far of phone numbers or physical addresses being involved, only email addresses paired with tax-related data. Still, that combination alone can be enough to create serious leverage for extortion attempts.
What This Signals for the Industry
This incident underscores a shift in threat models. Non-custodial services are no longer safe by default. Any platform holding identifiable information connected to crypto activity is now a viable target. As adoption grows and reporting requirements expand, data pools become richer and more attractive to attackers.
The industry’s emphasis on key security remains important, but it’s incomplete. Data protection, access controls, and breach response are becoming just as critical.
Conclusion
Waltio’s situation is a reminder that crypto risk doesn’t stop at custody. As personal data becomes increasingly tied to on-chain activity, attackers are following the trail. The next phase of crypto security won’t just be about protecting coins. It will be about protecting the identities behind them.